| In summary |
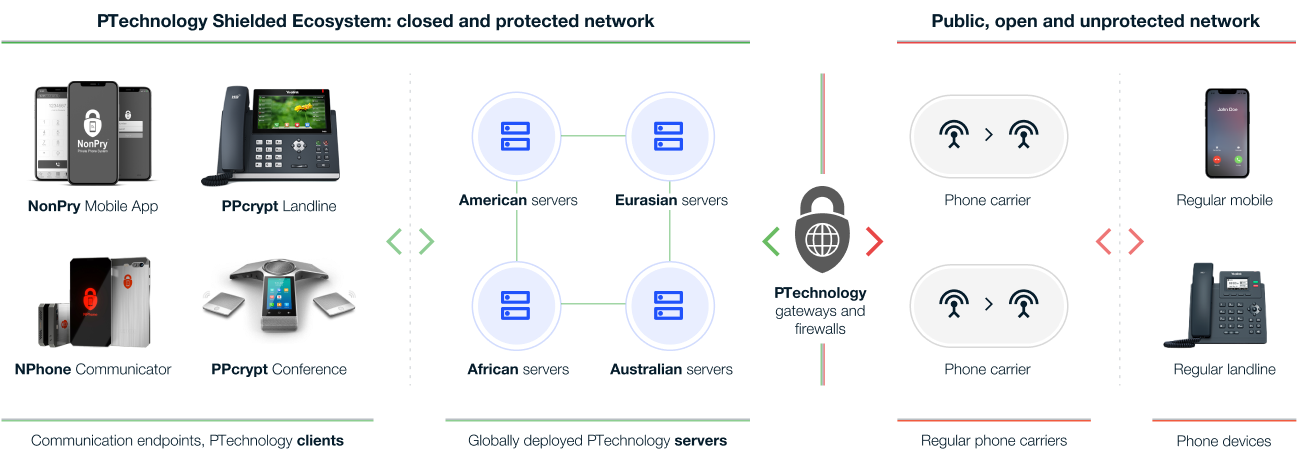
Inside PTechnology Shielded Ecosystem, the communication is safe, protected, unsaved, unstored, and entirely free. No one can intercept your calls. |
Your privacy is protected, if you do not use outgoing ID, except if the listeners are using voice recognition. |
Your calls are unsecure, tappable, your contact network is traceable and easily visualisable. Avoid sensitive calls, especially if you are a priority person. |
| Connection security |
Protected, untappable, multi-layered channel and data encryption, including SRTP/ZRTP-TLS |
PTechnology: secure until public ecosystem
Regular providers: tappable + backdoors |
Notoriously vulnerable, easily hackable, interceptable, especially the GSM communication. |
| Communication and call logs |
No call logs generated: in the system, no data are saved or stored. |
PTechnology: no data saved or stored
Regular providers: save and stored |
Logs of calls and messaging are created, stored, and bound to your personal and financial data. Every of your calls and messages are tracable. |
| Personal and financial data |
No financial data are stored, and we only need an email address during a registration, which is not bound to any communication data. |
PTechnology: not saved or bound
Regular providers: saved, stored, bound |
Regular providers collect, save, store and process every data in their big data systems. A hostile government can request for your profile easily. |
| Local calls |
Completely free and limitless |
Very low call rates |
According to current rates |
| International calls |
Completely free and limitless |
Very low call rates |
Expensive international call rates |
| Roaming fee |
No roaming fees |
No roaming fees, our system is global |
It depends on the concrete country, but usually, yes. |
| International conference calls - between 3 continents |
Completely free, protected, untappable and untraceable with crystal clear HD audio and video calls. |
Because of the public network, the call is traceable, tappable, the sound quality is worst, and the call is not free. |
In case of international businesses, 99% probability that someone is following your calls. The sound quality is poor, and the call is expensive. |